Sunday, April 26, 2020
Confinamiento
 |
| Figura 1: Confinamiento |
El café sabe amargo, ya os lo he dicho. Podría haber elegido una taza de café "normal", pero entonces no cabría tanto. Y no quiero vivir la vida a sorbos. Y tampoco soy de pensar que solo hay una forma de hacer las cosas de manera "normal". Nunca lo he sido. Me gusta pensar que eso no es ser hacker. También podría haber sacado una taza de Star Wars, de las grandes, pero esas son de mi colección.
Me apego a recuerdos. A mis pequeñas cosas que cuando las miro con la realidad aumentada de mi mirada están llenas de historias vivas que danzan frente a mis ojos. En 3D. Con música envolvente. Son casa. Son refugio. Me gusta alejarme un poco de ellos para crear nuevos recuerdos. Solo un poco. Para volver a disfrutarlos más. Y los objetos y recuerdos que vienen conmigo son yo. Son parte de mí, fueran dulces o amargos.
El café sabe amargo, pero no es intenso. Me gusta americano. Largo de agua. Aguachirri. Como lo pido siempre cuando quiero café. Sin leche. Largo como mi jornada laboral. Largo y amargo. Largo como mi pasado. Largo, espero, como mi futuro. Para sentir la experiencia durante más tiempo. Solo un poco más. Nada dura para siempre salvo en la memoria donde el tiempo se pliega. Como en la película esa de "Origen". Un sueño dentro de otro. Recursivo como los algoritmos. No se acaba. Ni lo dulce ni lo amargo. Pero el sabor del café es amargo. Y no quiero vestirlo de algo dulcificado echando mucha azúcar. Un poco para hacerlo más llevadero, puede, pero no mucho más maquillaje. Quiero sentir las cosas como son. Que duelan si tienen que doler. Que amarguen si tienen que amargar.
Mis ojos ya no son lo que eran. Están más cansaditos. Empiezan a pedir tregua de tanta lectura. De tantas letras en pantallas. De tantos mensajes que releí. De tantas y tantas hojas luchando contra mis párpados. De mi cerebro ávido por captar más de todo lo que se ve y lo que no se ve. De tantas luces en aventuras galácticas. Series de superhéroes. O de zombies que decoran el paisaje o antihéroes que van a acabar mal porque toman malas decisiones constantemente intentando avanzar. O porque la serie ya comenzó en un psiquiátrico como declaración de intenciones de lo que nos esperaba por delante.
Mis ojos ya no son lo que eran. Me piden ayuda. Mis ojos. Y se la doy a dosis pequeñas. No quiero que se acomoden. Aún no. Quiero que peleen por descifrar el mundo con sus propias herramientas. Pero de vez en cuando los consuelo. Les echo un poco de azúcar. Dejo que se acunen sobre el cristal de unas lupas de lectura. Para que aguanten más. Para que me descifren el mundo unos minutos más antes de caer rendido en la negrura de la noche.
El día es gris. Igual que ayer. Igual que el otro domingo que hizo buen día. Lo veo desde aquí. Mi sitio es el mismo que llevo ocupando durante este último mes y algo. Un rincón de la existencia con una ventana por la que veo solo un poquito del mundo analógico cuando mi foco se relaja. Solo una esquina de la vida. Por la que miro mientras me amargo mi paladar con el sabor del café. Con las gafas puestas para leer esa presentación con números y letras pequeñitas. Es mi vida. Casi enteramente mi vida es esto ahora.
El día es grande. O será que yo me siento pequeño. Como seguro que te sientes tú. Porque es como si me escondiera. Me siento un poco azul. No. No lo tomes mal. No me disgusta el color. Ni el gris ni el azul. La vida no es solo sol. La vida no es solo color amarillo. No solo luz. El azul es bonito también. Me gusta su olor. Su tacto. Y acurrucarme un rato con una de mis muchas bolitas azules. Esas que tengo en la estantería. Cojo una un rato. Me abrazo a ella. Retozo en mi sofá acurrucándola. O mirando al cielo con mi taza de Winnie The Pooh.
Mi cerebro vuela. Por el cielo. Sé que pronto saldré a jugar con las bolas amarillas. Sé que volveré a salir al parque a jugar con mis amigos. A gritar. A dar abrazos y besos. A ver un partido de fútbol. A ir a escuchar a los poetas rasgar sus guitarras. A sudar. A escuchar los gritos. A pegar los chillidos. A destrozar las canciones por no saber cantar. A mezclar el rojo con el amarillo. A mezclar el amarillo con el azul. A trepar por el monte con mi bicicleta cual motivado. A escuchar la música mientras vagabundeo en soledad por el mundo. Ese al que solo viajo yo. Por otros países. A irme a retozar con Morfeo sin tener que pelear por ello. Correr a sus brazos sin hacer cola en la frontera.
Mis palabras se amontonan. Están ahí. Guardadas. Para ti. Para las cenas. Para las charlas. Para las confesiones. Para los reencuentros. Para cuando las quieras oír. Para cuando las puedas escuchar de mi voz. Para que no sea algo digitalizado. Para que sea el sonido que emito con mis cuerdas vocales directamente. Ese que conecta directo con el motor de mi cuerpo. Ese que escribe cosas que nadie lee. Que nadie escucha. Que nadie le dicta. El inventor de los sentimientos. El pintor de las bolitas.
Mis caricias te extrañan. En los confines de mis dedos. Las noto palpitar cuando golpeo con suavidad las teclas de mi teclado. Cuando escribo algo para nadie. Pidiendo salir. Pidiendo espacio para ellas. Para que no duelan los dedos al final del día por el repiquetear constante. Para que el cansancio no sea solo mecánico sino también cuántico. Para que los dedos se muevan como olas al compás de dunas de ese desierto inmenso en soledad que queda por recorrer. Una vez más. Lentas. Eléctricas. Quemando. Como un calambre que sube por mis antebrazos y enciende el tatuaje imaginario de las llamas que nunca me hice.
La vida sigue escribiendo grietas en mi cara con tinta indeleble. En los surcos de mi piel. Donde guardo lo importante. Las risas. Los recuerdos. Los anhelos. Los planes inconclusos. Los conclusos. Con todos los metadatos. Con los recuerdos que he querido convertir en yo. En casa. Lo mejor de historia, de física y química. De arte. O incluso de filosofía sobre la vida que iba a tener pero que nunca tuve.
Mi pasado se perdió en este futuro. Porque de los mil caminos del multiverso el premio cayó en otra línea temporal. Porque la banda cambió el setlist por el camino. Porque fallé el pie de una estrofa. Porque no afinamos la canción en el mismo tempo. O porque mi diapasón se rompió por usarlo tanto a tanta velocidad. Y cada día puedo leerlos con más intensidad. Cuando me miro al espejo. Las canciones que salieron al final para el elepé son las que tengo escritas en mis arrugas. Pero aún me queda discografía que componer. Ouh, yeah!
Mis huesos me gritan. Cuando subo o bajo una escalera. Cuando recuerdo los golpes en la cadera al caerme de los patines. Cuando me levanto de la silla para preguntarle al sol qué hora es. Cuando pienso en todas las veces que necesito caerme aún. Cuando me veo volando sobre una tabla. Cuando recuerdo la negrura que viene tras la rampa. Cuando me despierto de la oscuridad y me están cosiendo la cabeza. Con sangre en los ojos. Cuando pienso en que el dolor no existe cuando el golpe es suficiente certero como para abrirte la cabeza. Y te quedas en calma para siempre. Mis huesos malvados me gritan. A veces bajito. Otras como lo hago yo cuando necesito quemar energía. O echar fuera todo.
Mi alma no te ve. No sabe donde estás. No sabe dónde te escondes. Donde se mete la gente cuando se acaba la conferencia. Donde te vas cuando acabo mi charla. Cuando me quito el gorro. Cuando ya no tengo el micrófono conectado. Cuando las fotos se acabaron. Donde estas ahora que mi mundo es este café amargo. Esta ventana analógica al mundo. Este sorbo tan pequeño de lo que es vivir. Donde todos los recuerdos bonitos de este confinamiento son solo terciopelo.
Mi televisión llora. Cuando da las noticias. Cuando dan números y números. Curvas. Gráficas. Tendencias. Nunca pensé que las matemáticas pudieran ser tan dolorosas. Cuando yo me presentaba a subir nota en matemáticas si sacaba menos de un notable. Y tengo que limpiar la pantalla con un pañuelo. Porque si no limpias las lágrimas se enraízan y ya no salen como el rocío. Y se congelan. Y el hielo corta los órganos blandos del interior. Los que están cerca de tu corazón.
Solo queda batirse. Y resistir. Y volver al mundo que está ahí fuera. Al círculo de tus brazos. Al calor de esa botella de vino. A abrazar a mi mamá con fuerza. A celebrar los cumpleaños, los santos, los acontecimientos que nos hemos saltado. A caerse al suelo y hacerse una herida en la rodilla tropezándose al correr lejos, muy lejos. A abollar el mundo saltando. A tumbarse exhausto al descender de la bicicleta por el calor, y meterse en una fuente para refrescarse del calor. A sentir cómo se te cuartea la piel con el aire y el sol de la montaña. A bucear buscando peces en mar. A chocar unas cervezas al aire con unos amigos en la barbacoa.
Saludos Malignos!
Autor: Chema Alonso (Contactar con Chema Alonso)
Saturday, April 25, 2020
How To Start | How To Become An Ethical Hacker
- Have No Experience With Cybersecurity (Ethical Hacking)
- Have Limited Experience.
- Those That Just Can't Get A Break
- What is hacking?
There's some types of hackers, a bit of "terminology".
White hat — ethical hacker.
Black hat — classical hacker, get unauthorized access.
Grey hat — person who gets unauthorized access but reveals the weaknesses to the company.
Script kiddie — person with no technical skills just used pre-made tools.
Hacktivist — person who hacks for some idea and leaves some messages. For example strike against copyright.
- Skills required to become ethical hacker.
- Curosity anf exploration
- Operating System
- Fundamentals of Networking
PHASES OF HACKING
Hacking is broken up into six phases:The more you get close to all phases,the more stealth will be your attack.
1-Reconnaissance-This is the primary phase of hacking where hacker tries to collect as much as information as possible about the target.It includes identifying the target,domain name registration records of the target, mail server records,DNS records.The tools that are widely used in the process is NMAP,Hping,Maltego, and Google Dorks.
2-Scanning-This makes up the base of hacking! This is where planning for attack actually begins! The tools used in this process are Nessus,Nexpose,and NMAP. After reconnaissance the attacker scans the target for services running,open ports,firewall detection,finding out vulnerabilities,operating system detection.
3-Gaining Access-In this process the attacker executes the attack based on vulnerabilities which were identified during scanning! After the successful, he get access to the target network or enter in to the system.The primary tools that is used in this process is Metasploit.
4-Maintaining Access-It is the process where the hacker has already gained access in to a system. After gaining access the hacker, the hacker installs some backdoors in order to enter in to the system when he needs access in this owned system in future. Metasploit is the preffered toll in this process.
5-Clearning track or Covering track-To avoid getting traced and caught,hacker clears all the tracks by clearing all kinds of logs and deleted the uploaded backdoor and anything in this process related stuff which may later reflect his presence!
6-Reporting-Reporting is the last step of finishing the ethical hacking process.Here the Ethical Hacker compiles a report with his findings and the job that was done such as the tools used,the success rate,vulnerabilities found,and the exploit process.
Continue reading
Linux Command Line Hackery Series - Part 4
Welcome back to Linux Command Line Hackery, hope you have enjoyed this series so far. Today we are going to learn new Linux commands and get comfortable with reading text files on Linux.
Suppose that you wanted to view your /etc/passwd file. How will you do that? From what we have learned so far what you'll do is type:
cat /etc/passwd
And there you go, but really did you see all the output in one terminal? No, you just ended up with last few lines and you'll have to cheat (i,e use graphical scroll bar) in order to see all the contents of /etc/passwd file. So is there a command line tool in linux with which we can see all the contents of a file easily without cheating? Yes, there are actually a few of them and in this article we'll look at some common ones.
Command: more
Syntax: more [options] file...
Function: more is a filter for paging through text one screenful at a time. With more we can parse a file one terminal at a time or line by line. We can also go backward and forward a number of lines using more.
So if we're to use more on /etc/passwd file how will we do that? We'll simply type
more /etc/passwd
now we'll get a screenful output of the file and have a prompt at the bottom of terminal. In order to move forward one line at a time press <Enter Key>. Using enter we can scroll through the file one line at a time. If you want to move one screen at a time, you can press <Space Key> to move one screen at a time. There are more functions of more program, you can know about them by pressing <h key>. To exit out of more program simply type <q key> and you'll get out of more program.
Command: less
Syntax: less [options] file...
Function: less is similar to more but less has more functionality than more. less is particularly useful when reading large files as less does not have to read the entire input file before starting, so it starts up quickly than many other editors.
less command is based on more so what you've done above with more can be done with less as well. Try it out yourself.
Command: head
Syntax: head [OPTION]... [FILE]...
Function: head command prints the head or first part of a file. By default head prints out first 10 lines of a file. If more than one file is specified, head prints first 10 lines of all files as a default behavior.
If we want to see only first 10 lines of /etc/passwd we can type:
head /etc/passwd
We can also specify to head how many lines we want to view by using the -n flag. Suppose you want to see first 15 lines of /etc/passwd file you've to type:
head -n 15 /etc/passwd
Ok you can view the first lines of a file what about last lines, is there a tool for that also? Exactly that's what our next command will be about.
Command: tail
Syntax: tail [OPTION]... [FILE]...
Function: tail is opposite of head. It prints the last 10 lines of a file by default. And if more than one file is specified, tail prints last 10 lines of all files by default.
To view last 10 lines of /etc/passwd file you'll type:
tail /etc/passwd
and as is the case with head -n flag can be used to specify the number of lines
tail -n 15 /etc/passwd
Now one more thing that we're going to learn today is grep.
Command: grep
Syntax: grep [OPTIONS] PATTERN [FILE...]
Function: grep is used to search a file for lines matching the pattern specified in the command.
A PATTERN can simply be a word like "hello" or it can be a regular expression (in geek speak regex). If you aren't familiar with regex, it's ok we'll not dive into that it's a very big topic but if you want to learn about it I'll add a link at the end of this article that will help you get started with regex.
Now back to grep say we want to find a line in /etc/passwd file which contains my user if we'll simply type:
grep myusername /etc/passwd
Wohoo! It gives out just that data that we're looking for. Remember here myusername is your username.
One cool flag of grep is -v which is used to look in file for every line except the line containing the PATTERN specified after -v [it's lowercase v].
Take your time practicing with these commands especially grep and more. We'll learn a lot more about grep in other upcoming articles.
References:
https://en.wikipedia.org/wiki/Regular_expression
http://www.regular-expressions.info/
Awesome website to learn Regular expressions - http://www.regexr.com/
Related links
Top 20 Android Spy Apps That Will.Make U Fell Like A Dectitive
Top 10 Best android spy apps.
t's worth to note that there are plenty of Android spy apps available on the Google Play Store, but mentioning all of them is not possible. So, in this article, we have listed the one that's popular and used by many. So, let's explore the list of best spy apps 2019.
#1 Spy Camera OS

This app permits users to capture images secretly. This app provides a smart way to shoot photos with a hidden camera interface so people wouldn't notice that you are taking pictures of them. Also, every sound and flash etc get disabled in this app.
#2 Ear Spy

This is an awesome app to record even low voices. By this app, you can place your phone in the other room and can listen to the voices of that room by your Bluetooth handset. This app actually records the sound and then amplifies its recording and give you the amplified clear voices.
#3 Ip Cam Viewer
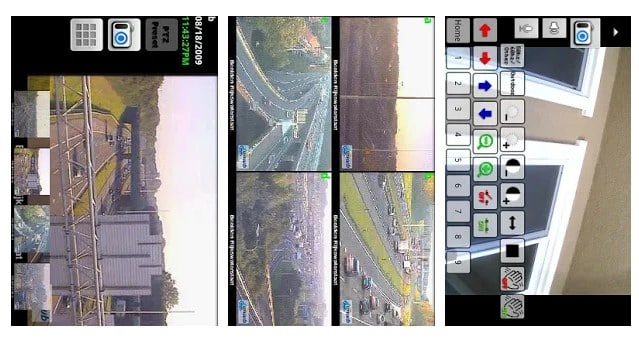
This awesome app allows to remotely view and control your IP Camera, DVR, Network Video Recorder, traffic cameras, CCTV or WebCam from an android device. In its new version, you can also get the notification on detecting motion on the device. This app can automatically start recording whenever it detects motion.
#4 Automatic Call Recorder
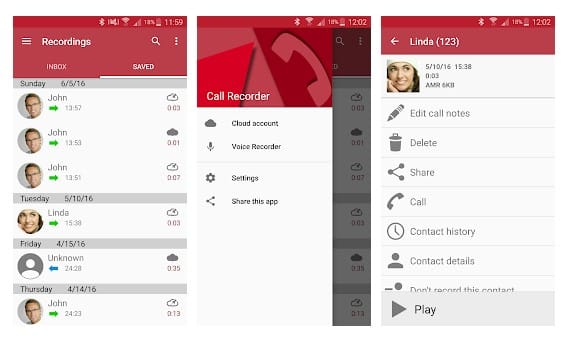
This is another best Spy App that one can have on their Android smartphone. This app gets automatically launched whenever you make or receive any call. It records all the conversation b/w speakers and also the surrounding noise of the device in which it is installed.
#5 Monitor Call Sms Location

This is another good spy app to remotely monitor SMS, Photo, Location, call logs and many more things on an Android device. This will exact location of the targeted device through a web-portal even if GPS disabled on the target device. The app comes with the three-day free trial option.
#6 Anti Spy Mobile
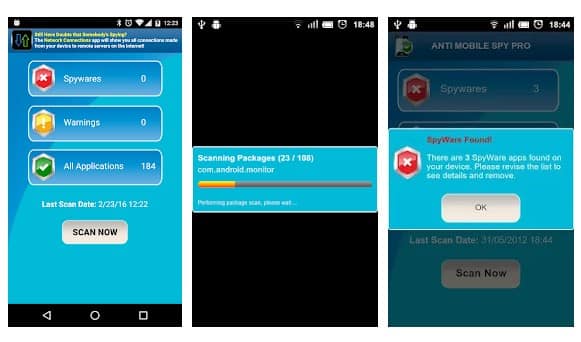
You don't know whether you had installed any spyware software on your phone? Use this app to instantly find the spyware. The Android app uses advanced detection techniques to detect new spyware. So, with this app, you can easily protect yourself from Android spyware.
#7 Hidden Eye
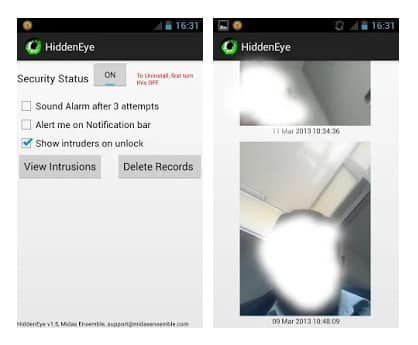
Ever wanted to know who tried snooping on your phone while you were away. Your friends or family member might have tried to unlock your phone. Hidden Eye is a simple app with no frills that will photograph the person when they try to unlock your phone.
#8 AppLock

Applock is the most downloaded app lock in Play Store. Protect privacy with password, pattern, fingerprint lock. AppLock can lock Facebook, Whatsapp, Gallery, Messenger, SMS, Contacts, Gmail, Settings, incoming calls and any app you choose. Prevent unauthorized access and guard privacy. Ensure security.
#9 Hide Calls Automatically

With this app, all outgoing, incoming and missed calls coming from private contacts will be deleted automatically from calls Log of your phone! No icon of this app will appear in your list of applications on your phone.
#10 Truecaller: Caller ID & Dialer
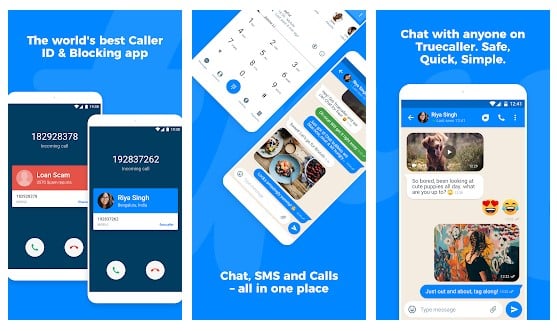
Truecaller is the only dialer you'll ever need with the ability to identify unknown callers and block unwanted calls. See names and photos of people who call, even if they aren't saved in your phonebook. And know when friends are free to talk, making your calling experience smarter and more delightful.
#11 Cell Tracker
![]()
You can use the cell tracker Android app to keep track of the location of your smartphone. With the help of this app, you can track all the locations you have visited in the last few days with your Android phone. To check the locations visited you have to launch the app and click on "View Now". No need to turn on the GPS.
#12 Secret Calls

With the help of this app, all outgoing, Incoming and Missed Calls coming from private contacts will be deleted automatically from Calls Log of your phone! No icon of this app will appear in your list of applications on your phone.
#13 Spy Camera

This is another Spy app on the list which provides one-touch to capture image feature. The app actually has lots of useful features. With the help of this app, you can find your lost phone because this app allows you to set up a number. When you lost your phone, just SMS to this phone and it will take a picture and upload to drive.
#14 Truecaller

Truecaller is a popular Android app which is used every day to identify unknown calls, block spam calls and spam SMS. It filters out the unwanted and lets you connect with people who matter.
#15 Whoscall – Caller ID

Whoscall, the best caller ID App that identifies unknown calls and blocks annoying spams, robocall & telemarketing with more than 50 million downloads and over 1 billion numbers data. It also got the call blocker that can be used to blacklist or whitelist contacts stored on your smartphone.
#16 Norton Family parental control
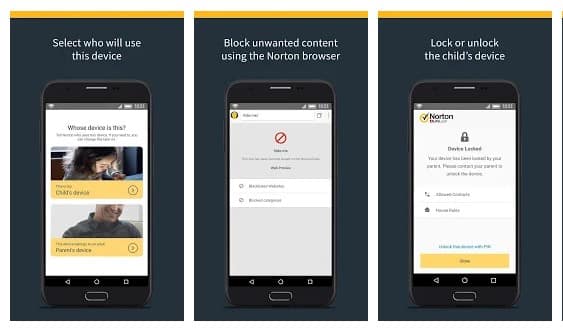
Norton Family parental control is basically an Android app that is meant to keep kids safe online. However, this is nothing sort of a spy app. The app can help you to supervise online activity. You can easily keep track of sites which your friend visit and what they search if you install Norton Family Parental control on their phone.
#17 Smart Hide Calculator

The app doesn't help users to spy on others. But, it can give you a detective type feeling. Smart hide calculator is a fully functional calculator app but with a little twist. Once you enter the password and press the '=' button then boom you are presented to an interface where you can hide, unhide pictures, videos, documents or files with any file extension.
#18 Hidden Eye

Ever wanted to know who tried snooping into your phone while you were away. Your friends or family member might have tried to unlock your phone. Hidden Eye is a simple app with no frills that will photograph the person when they try to unlock your phone.
#19 Background Video Recorder
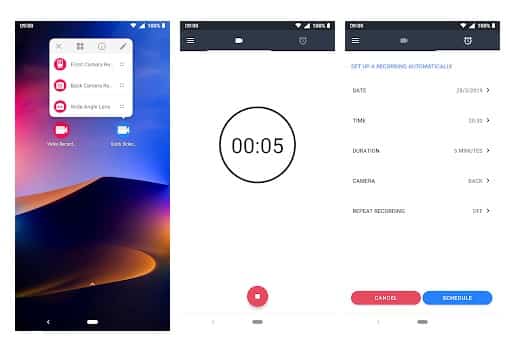
This is another best Android spy app that helps users to record what's happening behind them. Background Video Recorder is basically a camera app that records videos silently on the background. The app eliminates the camera shutter sounds, camera previews and it can also record videos when the screen is off.
#20 Kids Place

Kids Place is another best parental control app in the list and its meant to protect your kids' online activities. However, if you don't have kids, you can use the app to track other devices. The app gives you full control over other devices and you can control everything including calls, text, internet browsing, apps, etc.
@EVERYTHING NT
Continue reading
RapidScan: The Multi-Tool Website Vulnerabilities Scanner With Artificial Intelligence
- One-step installation.
- Executes a multitude of security scanning tools, does other custom coded checks and prints the results spontaneously.
- Come of the tools include
nmap,dnsrecon,wafw00f,uniscan,sslyze,fierce,lbd,theharvester,dnswalk,golismeroetc executes under one entity. - Saves a lot of time, indeed a lot time!
- Checks for same vulnerabilities with multiple tools to help you zero-in on false positives effectively.
- Legends to help you understand which tests may take longer time, so you can Ctrl+C to skip if needed.
- Association with OWASP Top 10 2017 on the list of vulnerabilities discovered. (under development)
- Critical, high, large, low and informational classification of vulnerabilities.
- Vulnerability definitions guides you what the vulnerability actually is and the threat it can pose
- Remediations tells you how to plug/fix the found vulnerability.
- Executive summary gives you an overall context of the scan performed with critical, high, low and informational issues discovered. (under development)
- Artificial intelligence to deploy tools automatically depending upon the issues found. for eg; automates the launch of
wpscanandplecosttools when a wordpress installation is found. (under development) - Detailed comprehensive report in a portable document format (
*.pdf) with complete details of the scans and tools used. (under development)
For Your Infomation about RapidScan:
- Program is still under development, works and currently supports 80 vulnerability tests.
- Parallel processing is not yet implemented, may be coded as more tests gets introduced.
RapidScan supports checking for these vulnerabilities:
- DNS/HTTP Load Balancers & Web Application Firewalls.
- Checks for Joomla, WordPress and Drupal
- SSL related Vulnerabilities (HEARTBLEED, FREAK, POODLE, CCS Injection, LOGJAM, OCSP Stapling).
- Commonly Opened Ports.
- DNS Zone Transfers using multiple tools (Fierce, DNSWalk, DNSRecon, DNSEnum).
- Sub-Domains Brute Forcing.
- Open Directory/File Brute Forcing.
- Shallow XSS, SQLi and BSQLi Banners.
- Slow-Loris DoS Attack, LFI (Local File Inclusion), RFI (Remote File Inclusion) & RCE (Remote Code Execution).
- Kali Linux, Parrot Security OS, BlackArch... Linux distros that based for pentesters and hackers.
- Python 2.7.x
RapidScan's screenshots:
 |
| RapidScan helping menu |
 |
| RapidScan Intro |
 |
| RapidScan Outro |
How to contribute? If you want to contribute to the author. Read this.
More info
Friday, April 24, 2020
WHY WE DO HACKING?
. Just for fun
.Show-off
.Steal important information
.Damaging the system
.Hampering Privacy
.Money Extortion
.System Security Testing
.To break policy compliance etc
BeEF: Browser Exploitation Framework
 "BeEF is the browser exploitation framework. A professional tool to demonstrate the real-time impact of XSS browser vulnerabilities. Development has focused on creating a modular structure making new module development a trivial process with the intelligence residing within BeEF. Current modules include the first public Inter-protocol Exploit, a traditional browser overflow exploit, port scanning, keylogging, clipboard theft and more." read more...
"BeEF is the browser exploitation framework. A professional tool to demonstrate the real-time impact of XSS browser vulnerabilities. Development has focused on creating a modular structure making new module development a trivial process with the intelligence residing within BeEF. Current modules include the first public Inter-protocol Exploit, a traditional browser overflow exploit, port scanning, keylogging, clipboard theft and more." read more...Website: http://www.bindshell.net/tools/beef
Related links
Thursday, April 23, 2020
How To Install And Run Backtrack On Android
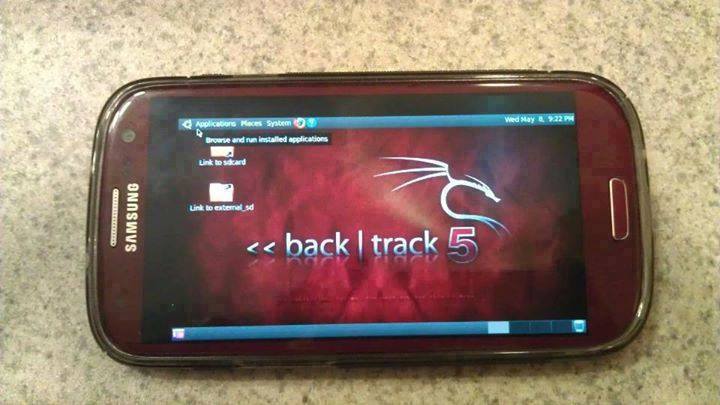
- A Rooted Device [ Root Simple Android Phone Without Pc ]
- Backtrack ARM [ Download ]
- BusyBox [ Download ]
- Android Terminal and Android VNC
- If you are using PC then you need 7zip for extraction otherwise you can use zarchiver on your android phone. [ Download ]
- Now install all the above apps Busybox, Android Terminal, Android Vnc.
- After installing BusyBox application open it and wait until it finishes loading and then click on Smart install.
- Now open the android terminal and type the following command:
su cd /sdcard/BT5sh bootbtNOTE :- When you type su in terminal it will ask you for superuser request and you have to tap on Grant. - After this, type the following commands in terminal.
export USER=rootvncpasswd - After entering vncpasswd the terminal will ask you to enter the password. Enter the desired password and hit enter.
- Now type the following commands.
tightvncserver -geometry 1280×720 - The terminal emulator will create the localhost to connect it to VNC server. Now note the localhost port marked red below. Now minimize the terminal emulator.
- Open the Android VNC and type the following settings.
Password : your password here which you entered in terminal (step no.6)
Address : localhost
Port : 5906






